Call me paranoid, but I think Google Glass is scary.
Sergey Brin's live demonstration of Google Glass at the Google I/O Conference last month clearly showed that wearable, always-on, Web-connected computing technology is here now, and that it works. It's coming from one of the wealthiest companies in the world, a company that might become a lot wealthier if Google Glassaccomplishes in the physical realm what the Web browser has done for Google in the digital realm.
Let me explain. Google has amassed immense power by cataloging and analyzing the Internet, as well as selling ads there. They are masters of that universe. Like many other tech companies, however, Google isn’t satisfied with such a confined sphere of influence. Google has been searching for ways to treat things in the real world the way it treats things in the digital domain, by numbering, locating, mapping, cataloging, and analyzing them. Google became the giant it is today by making stuff on the Web searchable. Does the company see its second golden age in making things in the real world searchable?
Some companies have tried to affix QR codes to objects, placing a digital marker on real-world things and thereby giving those objects representation in cyberspace. QR codes have seen limited success, but that technology is just a cheap parlor trick next to the powerful Web-enabling technology that is Google Glass.
Always-On Augmented Reality
Google Glass resembles a sleek pair of reading glasses, except the narrow lens sits slightly above one eye. Basically a tiny see-through computer monitor, the lens can overlay data and images atop the user's field of vision, delivering incoming messages, video, maps, or anything else that can transmit wirelessly from a Web server. Google Glass also incorporates a miniaturized smartphone equipped with cameras, a microphone, a Web browser, and speech-recognition capabilities.
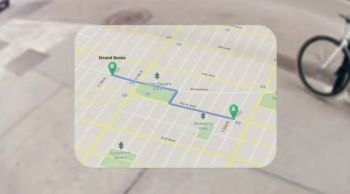
For instance, reacting to a spoken location-search command from the user, the glasses might overlay directions to that specific place, and show identification labels over landmarks along the way. The potential is even wilder--the glasses might display directions on how to react in a medical emergency, complete with CPR demonstration videos and a real-time video chat with a physician.
Such intelligence flowing into the glasses for the wearer’s benefit is good; it’s the information that might flow out of the glasses that worries me. Since Google Glass is connected to the Internet via a fast wireless connection, it could easily report what the wearer is seeing, hearing, and doing in real time.
On the Web, Google has become extremely proficient in tracking users' movements through cookies, and then employing massive analytics to predict people's likes, interests, and likelihood to buy. Could Google use Glass as a platform to track and analyze our movements in the real world?
A Marketer’s Dream--and a Consumer's Nightmare?
What’s to prevent Google from tracking the movements of our eyeballs to discover the things that catch our attention? When I walk out of my apartment building, for example, a car might pass by that turns my head; I might glance at it in spite of myself. Could the Google Glass technology form a heat map showing the things my eyes rested on? Perhaps someday the technology will be able to measure how fast and how far I turned my head to look at something, and then develop a likelihood-to-buy score based on that. Call it the Whiplash Index.
Capturing that kind of data is the stuff of fantasy for marketers, a simple and direct indication of which types of ads to push at the viewer, and when to deliver them. And that's one of the most likely abuses of Google Glass: The device might display ads that are “contextual.” In other words, the subject matter of the ads may be driven by objects in the wearer’s field of vision, or in the general environment surrounding the wearer.
Marketers could partially target such ads via existing location-based technology. For instance, Glass might display a coupon for a free cup of coffee when it detects that the wearer is walking near the advertised coffee shop (GPS would reveal this), and that the wearer has glanced over at the coffee shop at least twice along the way.
Ultimate Surveillance
Then there’s facial recognition. That technology is unsettling enough when it identifies faces in still pictures or recorded video. But if Google Glass were connected to a server that could recognize faces, facial recognition could happen in real time. Potentially, the wearer could scan a crowd of people and see labels above those who happened to be friends of friends of friends in Google+. Sure, phone apps that do this already exist, but Glass would make such apps far simpler to use, and easier to leave running all the time.
This might not be a big deal if just a few people in every city were to end up wearing Google Glass. But what if the device were to catch on, becoming as big as the iPhone is today? All those glasses would be collecting monstrous amounts of audio and video information every minute of every day, possibly piping the data through the network for storage in some vast server farm. Yes, in the 21st century, Big Brother lives on a farm.
Judging from the wording of Google’s overarching privacy policy and terms of use, the sounds and images that Google Glass records would not be the property of the person wearing the glasses. Google could use those sounds and images for whatever it wants.
As long as we’re talking about worst-case scenarios: What if another horrific terrorist attack were to occur on our soil, one even worse than 9/11? Some people say it’s not a matter of if, but when such an attack will occur. What if the attack involves something insidious like chemical or biological weapons, and is perpetrated by people living within the United States?
Our anxiety levels would skyrocket again, our government might take a renewed and even more aggressive interest in surveillance to detect bad actors in our midst, and frightened constituents might be willing to surrender big chunks of their privacy in exchange for a little reassurance and peace of mind. Our government could then give itself new powers to access information collected by technology companies that sell products and services like Google Glass. You won’t find a better surveillance tool than a bunch of people walking around recording everything they see and hear.
Not Evil, but...
These scenarios are horror stories that may never see the light of day, of course. Internet companies such as Google seem to have a healthy fear of crossing boundaries and prompting a privacy backlash that could hurt their bottom line.

But Google Glass might let the genie out of the bottle. Even if Google has no intention of using the glasses for anything but entertaining and informing users, the mere existence of the pile of real-time data collected could cause problems in the future.
Although Google may not do anything “evil” with the device, some other, smaller, poorer, and more desperate startup company might. For instance, if Google refused to enable Glass as a real-time facial-recognition tool, or as a wearable advertising platform, some other company might see those things as huge market opportunities.
The answer is not to ban or shun such technology. Some of the things that Google Glass does are undeniably cool and useful. But tech companies sometimes forget the maxim that just because you can invent something doesn’t mean you should “productize” it and turn it loose in the wild.
In the end, therefore, it’s up to us consumers to recognize potentially dangerous or privacy-infringing products and let the makers know that they’ve gone too far.